Create Self-Signed S/MIME Certificates
Sign and encrypt e-mail through public-key encryption using OpenSSL generated certificates

How do you send an e-mail containing sensitive information? Do you send anything and everything through e-mail without concern for prying eyes? Recent news stories about e-mail account hacks and interceptions by third-parties make me increasingly unwilling to send anything containing private information through standard plain-text e-mail. If you have been through the process of buying a home in the United States, the amount of sensitive information transferred back-and-forth between the various parties is staggering and, from my experience, it is primarily done through plain-text e-mail.
So, what can you do?
While this article does not address the larger systemic issues around private information transfer, it does provide a basic method for public-key encryption and signing of MIME data (e-mail) using the S/MIME standard. Most well-known e-mail clients support S/MIME and this article provides instructions for creating your own CA to create self-signed S/MIME certificates.
NOTE: I have tested these steps using the Win64 OpenSSL v3.6.1 Light (EXE) distribution available on the Win32/Win64 OpenSSL Installer for Windows - Shining Light Productions website.
A Very Brief Primer on Public-key Encryption
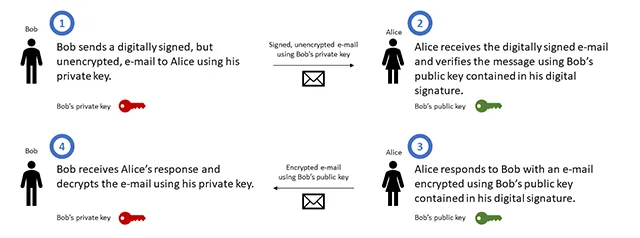
Since certificates are based on public-key encryption, also known as public-key cryptography or asymmetric cryptography, please keep in mind that the public key of the intended e-mail recipient is required in order to encrypt the e-mail. Conversely, if someone wants to send you an encrypted e-mail, that person needs your public key.
As an example, if Alice wants to send an encrypted e-mail to Bob, Alice needs Bob’s public key to encrypt the e-mail. When Bob receives the encrypted e-mail from Alice, Bob’s e-mail client uses his personal private key to decrypt the e-mail. If Bob wants to send Alice an encrypted e-mail, he needs Alice’s public key to encrypt the e-mail.
This article steps through the creation of a personal public/private key pair. The public key is what an e-mail sender needs to be able to encrypt an e-mail sent to you. Your private key is kept only by you since that is used to decrypt any e-mails encrypted using your public key. If your private key is obtained by anyone else, then that person is able to decrypt and read your encrypted e-mails.
Is There an Easier Way?
Yes. You can obtain a basic certificate for free from a number of companies. I will not list those companies because they tend to require a “free” sign-up and then they proceed to inundate you with spam.
However, by creating your own certificate, you do not rely on an external party and you get to learn a little bit more about public-key encryption along the way.
Instructions
Step 1: Install OpenSSL
We use OpenSSL to create a certificate authority. This certificate authority is then used to sign the personal certificate that we create. The latest OpenSSL toolkit is found at the OpenSSL website. If a binary distribution is needed, e.g., pre-compiled installation files for Microsoft Windows, I suggest using the distributions available at the Shining Light Productions website.
Once you’ve found the appropriate distribution for your operating system, please proceed with the installation instructions provided with that distribution.
I am using a Windows distribution so portions of this post may be specific to that operating system. Please also note that I have installed OpenSSL in the c:\openssl\ directory.
Step 2: Create an OpenSSL Configuration File
NOTE: This step may not be necessary depending on the particular OpenSSL distribution. In some OpenSSL distributions, the basic configuration file already includes the required extensions referenced below. In other distributions, a basic configuration file isn’t provided at all. If the default configuration file has the following extensions and you duplicate them in your own custom configuration file, then errors are thrown in Step 4 and Step 7. With the distribution I used (referenced above), there is a default configuration file containing the appropriate
[req],[req_distinguished_name], and[v3_ca]sections.
NOTE: With the distribution I used (referenced above), there is a default configuration file containing the appropriate
[req],[req_distinguished_name], and[v3_ca]sections so I do not need those sections in mysmime.cnf. However, I do usesmime.cnfand, specifically, the[smime]section to set the appropriate extensions in Step 7. If you are using the same distribution, the default configuration file may be found atc:\Program Files\Common Files\SSL\openssl.cnf.
Now that OpenSSL is installed, a configuration file is needed. If openssl.exe is executed at this point without the configuration file in place, the message WARNING: can't open config file: /usr/local/ssl/openssl.cnf is displayed.
Create a new file named smime.cnf containing the following configuration. The contents of the file follow the x509 certificate extension configuration format. For more information about the file format and content, please review the x509 v3 configuration page. The [req] and [req_distinguished_name] sections are generally part of any standard OpenSSL configuration file. Some distributions include a default configuration file that includes a version of these sections. I included them specifically in this configuration file because I was receiving an error message stating unable to find ‘distinguished_name’ in config and this resolved the error.
NOTE: The
[v3_ca]and[smime]sections are the important sections for this exercise because they set the appropriate extensions for an S/MIME certificate authority and personal certificates.
[req]
distinguished_name = req_distinguished_name
[req_distinguished_name]
countryName = Country Name (2 letter code)
countryName_default = AU
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Some-State
localityName = Locality Name (eg, city)
0.organizationName = Organization Name (eg, company)
0.organizationName_default = Internet Widgits Pty Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
emailAddress = Email Address
emailAddress_max = 64
[v3_ca]
basicConstraints = critical, CA:TRUE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always, issuer
[smime]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = emailProtection
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always, issuer
subjectAltName = email:copyNext, we set the OPENSSL_CONF environment variable to reference the new configuration file. Setting this environment variable eliminates the warning message mentioned earlier. This part is Windows specific. Recall that I have installed OpenSSL in the c:\openssl\ directory, named the configuration file smime.cnf, and saved it in the c:\openssl\ directory.
Open a command prompt window and be sure to Run as administrator if you are on Windows. Execute the following command:
set OPENSSL_CONF=c:\openssl\smime.cnfWhen openssl.exe is executed (from the c:\openssl\bin\ directory), there is no warning message and the OpenSSL> prompt is displayed. Type exit and you’ll be returned to the c:\openssl\bin\> prompt.
For those using Windows, if you ever need to remove the OPENSSL_CONF environment variable, then use the following command to launch the Environment Variables dialog box to create, edit, or delete user or system variables.
rundll32 sysdm.cpl,EditEnvironmentVariablesStep 3: Generate an RSA Private Key for the Certificate Authority
NOTE: The following steps and OpenSSL commands are executed from the command prompt (on Windows) and not in OpenSSL interactive mode.
In this post, we are creating a new certificate authority to sign personal certificates. Execute the following command to generate the RSA private key for the new certificate authority:
NOTE: Ensure all of the following commands are executed from a command prompt window started with
Run as administratorif you are on Windows.
openssl genrsa -aes256 -out ca.key 4096The options specify to use the aes256 encryption cipher and output the results to a file named ca.key with a size of 4096 bits. Please be aware that the corresponding public key is derived from this private key. No extra step or command is required to generate the public key.
The following message is displayed. Follow the prompts to create a pass phrase for this key. Remember this pass phrase for subsequent steps.
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:Step 4: Create Self-Signed Certificate for the Certificate Authority
NOTE: As mentioned in Step 2, if the distribution already has a proper configuration file, then the
smime.cnffile created in Step 2 is unnecessary and the last argument must be excluded from the command, i.e., remove-extensions v3_ca.
Execute the following command to generate the new self-signed certificate for the certificate authority:
openssl req -new -x509 -days 3650 -key ca.key -out ca.crt -extensions v3_caThe -x509 option outputs a self-signed certificate instead of a certificate request. The -days 3650 option specifies that the generated certificate is certified for 10 years (ignoring leap years). The -key option specifies the private key to use; the private key ca.key created in Step 3 is used. The self-signed certificate is written to a file named ca.crt using the -out option.
Follow the displayed prompts. Use the pass phrase from Step 3. I have left most fields blank by simply entering a . character. I have provided example entries below between the brackets following the prompts. Please change the values to meet your own particular needs.
Do not include the brackets in your entries.
Enter pass phrase for ca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:[.]
State or Province Name (full name) [Some-State]:[.]
Locality Name (eg, city) []:[.]
Organization Name (eg, company) [Internet Widgits Pty Ltd]:[EXAMPLE COMPANY]
Organizational Unit Name (eg, section) []:[.]
Common Name (e.g. server FQDN or YOUR name) []:[EXAMPLE COMPANY CERTIFICATE AUTHORITY]
Email Address []:[.]The certificate authority has been created. Now, we begin creating the personal certificate for a particular e-mail address.
Step 5: Generate an RSA Private Key for the Personal E-Mail Certificate
Similar to Step 3, we need to create a new private key. This private key is for your personal certificate instead of the certificate authority. Again, please be aware that the corresponding public key is derived from this private key. No extra step or command is required to generate the public key.
The example uses a fake person named Aida Bugg with an e-mail address of aida_bugg@example.com who works at EXAMPLE COMPANY (example.com). As always, please change the values to meet your own particular needs unless, of course, this happens to be your name and place of employment.
Execute the following command:
openssl genrsa -aes256 -out smime_aida_bugg.key 4096When prompted, enter a pass phrase that is different from the one used in the certificate authority private key.
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:Step 5 (Alternate): Generate an ECC Private Key for the Personal E-Mail Certificate
NOTE: This guide uses RSA to create a private key, but you can use other available cryptographic algorithms to generate a key. The following sequence is purely informational and demonstrates Step 5 using elliptic curve cryptography (ECC) instead.
To get a list of all available curve short names, execute the following command:
openssl ecparam -list_curvesThe output appears similar to the following list (shortened for this comment):
secp112r1 : SECG/WTLS curve over a 112 bit prime field
secp112r2 : SECG curve over a 112 bit prime field
secp128r1 : SECG curve over a 128 bit prime field
secp128r2 : SECG curve over a 128 bit prime field
secp160k1 : SECG curve over a 160 bit prime field
secp160r1 : SECG curve over a 160 bit prime field
secp160r2 : SECG/WTLS curve over a 160 bit prime field
secp192k1 : SECG curve over a 192 bit prime field
secp224k1 : SECG curve over a 224 bit prime field
secp224r1 : NIST/SECG curve over a 224 bit prime field
secp256k1 : SECG curve over a 256 bit prime field
secp384r1 : NIST/SECG curve over a 384 bit prime field
secp521r1 : NIST/SECG curve over a 521 bit prime fieldSelect an appropriate curve short name from the list and modify/execute the following command.
openssl ecparam -name secp384r1 -genkey -noout -out smime_aida_bugg.keyStep 6: Create the Certificate Signing Request
Now that we have a personal private key, we need to create a certificate signing request. This command looks similar to Step 4 where we created a self-signed certificate for the certificate authority. In this step, however, the options are slightly different because we are creating a certificate signing request instead of a self-signed certificate. We are creating a certificate signing request to have the certificate authority sign the certificate.
Execute the following command:
openssl req -new -key smime_aida_bugg.key -out smime_aida_bugg.csrWhen prompted, enter the pass phrase used to create the private key in Step 5. Again, I have left most fields blank by simply entering a . character. I have provided example entries below between the brackets following the prompts.
Do not include the brackets in your entries.
Please note that the Common Name used in this step should be different from the one used in Step 4. I also didn’t set a challenge password or company name in the final two entries.
Enter pass phrase for smime_aida_bugg.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:[.]
State or Province Name (full name) [Some-State]:[.]
Locality Name (eg, city) []:[.]
Organization Name (eg, company) [Internet Widgits Pty Ltd]:[EXAMPLE COMPANY]
Organizational Unit Name (eg, section) []:[.]
Common Name (e.g. server FQDN or YOUR name) []:[Aida Bugg]
Email Address []:[aida_bugg@example.com]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:Step 7: Sign the Certificate Using the Certificate Authority
NOTE: As mentioned in Step 2, if the distribution already has a proper configuration file, then the
smime.cnffile created in Step 2 is unnecessary and the last two arguments must be excluded from the command, i.e., remove-extfile c:\openssl\smime.cnf -extensions smime. Please confirm that the extensions listed in the[smime]section in the above configuration file exist in the default configuration before removing the last two arguments.
At this point, we are finally creating the personal self-signed certificate. The configuration file created in Step 2 is used to set the necessary extensions and the certificate authority is used to sign the new personal certificate.
Execute the following command (increment set_serial with each signing request):
openssl x509 -req -days 3650 -in smime_aida_bugg.csr -CA ca.crt -CAkey ca.key -set_serial 1 -out smime_aida_bugg.crt -addtrust emailProtection -addreject clientAuth -addreject serverAuth -trustout -extfile c:\openssl\smime.cnf -extensions smimeWhen prompted, enter the pass phrase for the certificate authority private key from Step 3.
Signature ok
subject=O = EXAMPLE COMPANY, CN = Aida Bugg, emailAddress = aida_bugg@example.com
Getting CA Private Key
Enter pass phrase for ca.key:NOTE: Repeat Steps 5 through 7 to create certificates for additional e-mail addresses. In Step 7, increment the
set_serial argument(or assign a new unique number) for each additional certificate.
Step 8: Package the Certificate into the PKCS12 Format
After all of that work, I imagine you’ll want to use your new self-signed digital certificate to send e-mail. Many e-mail clients need the certificate packaged in a standard format. This step bundles the necessary files into the PKCS #12 format.
Execute the following command:
openssl pkcs12 -export -in smime_aida_bugg.crt -inkey smime_aida_bugg.key -out smime_aida_bugg.p12NOTE: The
-legacyflag may be required for some devices or e-mail clients to recognize the.p12file as valid. For security reasons, this is not recommended as the-legacyflag enables use of deprecated or insecure algorithms.
When prompted, enter the pass phrase associated with your personal private key created in Step 5. Create another pass phrase which is used when importing the .p12 file into an e-mail client.
Enter pass phrase for smime_aida_bugg.key:
Enter Export Password:
Verifying - Enter Export Password:Summary
You now have your very own self-signed S/MIME certificate which can be used to send signed e-mails. This also allows others to send you encrypted e-mails by using your public key. Once your recipients provide you with their public keys, then you’ll be able to send encrypted e-mails to them as well.
Common Issues
Missing Key Usages and Extensions
The most common issue is associated with Step 7 where the required key usages are not included in the certificate due to an improper configuration file. If these extensions are not included in the certificate, then the mail client accepts the certificate for digital signatures or encryption.
To verify that the certificate includes the required extensions, execute the following command:
openssl x509 -in smime_aida_bugg.crt -purpose -noout -textThis command outputs a list of certificate purposes and extensions as well as the public key itself. Verify that the certificate includes the following:
- S/MIME signing = Yes
- S/MIME encryption = Yes
- X509v3 Key Usage = Digital Signature, Non Repudiation, Key Encipherment
- X509v3 Extended Key Usage = E-mail Protection
- Trusted Uses = E-mail Protection
Certificate purposes:
SSL client : No
SSL client CA : No
SSL server : No
SSL server CA : No
Netscape SSL server : No
Netscape SSL server CA : No
S/MIME signing : Yes
S/MIME signing CA : No
S/MIME encryption : Yes
S/MIME encryption CA : No
CRL signing : No
CRL signing CA : No
Any Purpose : Yes
Any Purpose CA : Yes
OCSP helper : Yes
OCSP helper CA : No
Time Stamp signing : No
Time Stamp signing CA : No
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: O = EXAMPLE COMPANY, CN = EXAMPLE COMPANY CERTIFICATE AUTHORITY
Validity
Not Before: May 17 19:20:33 2022 GMT
Not After : May 14 19:20:33 2032 GMT
Subject: O = EXAMPLE COMPANY, CN = Aida Bugg, emailAddress = aida_bugg@example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (4096 bit)
Modulus:
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage:
Digital Signature, Non Repudiation, Key Encipherment
X509v3 Extended Key Usage:
E-mail Protection
X509v3 Subject Key Identifier:
X509v3 Authority Key Identifier:
keyid:
X509v3 Subject Alternative Name:
email:aida_bugg@example.com
Signature Algorithm: sha256WithRSAEncryption
Trusted Uses:
E-mail Protection
Rejected Uses:
TLS Web Client Authentication, TLS Web Server AuthenticationCertificate Authority Trust
Since we are creating self-signed certificates instead of using a well-known certificate authority, no operating system or mail client recognizes nor trusts your certificate authority by default. Your certificate authority must be added to the operating system or mail client trust store before any personal certificates signed by that certificate authority are recognized and trusted as valid. By paying well-known providers for a certificate, you avoid this administrative hassle. This is the price you pay to do it yourself.